SAP Security Application Maintenance Support
- How long does it take for a person to be operational in the field of SAP security and permissions?
- How much do I need to have one or more vertically trained resources on SAP security within your organization?
- Do I really need to define an SAP Security group in my company? Also to ensure the various backups?
- What are the systems on which we operate
Indice
Outsourcing security SAP, how does it work?
An initial evaluation and audit of the current system is carried out. This is to understand how the authorization system is structured to date and what are the procedures used. Here are the main points of attention taken into account:
- Whether or not to use an RBAC concept (Role Base Access Control)
- Percentage of custom usage (such as authorization objects or custom transactions)
- Customer knowledge of SAP authorization logics
- Using standard security features (e.g. Compound and derived roles)
- Differences from SAP best practices
After the evaluation, the system is taken over. It is important to stress that the decision of "who does what" is always up to the customer. An external outsourcer should never determine which roles to assign.
It is also possible in some cases that taking over the system involves having to face a review of the SAP security model. In this case read here how it can be dealt with!
Normally there is a settlement period to be agreed jointly.
What are the activities of the service?
The main tasks that are included in the service are as follows:

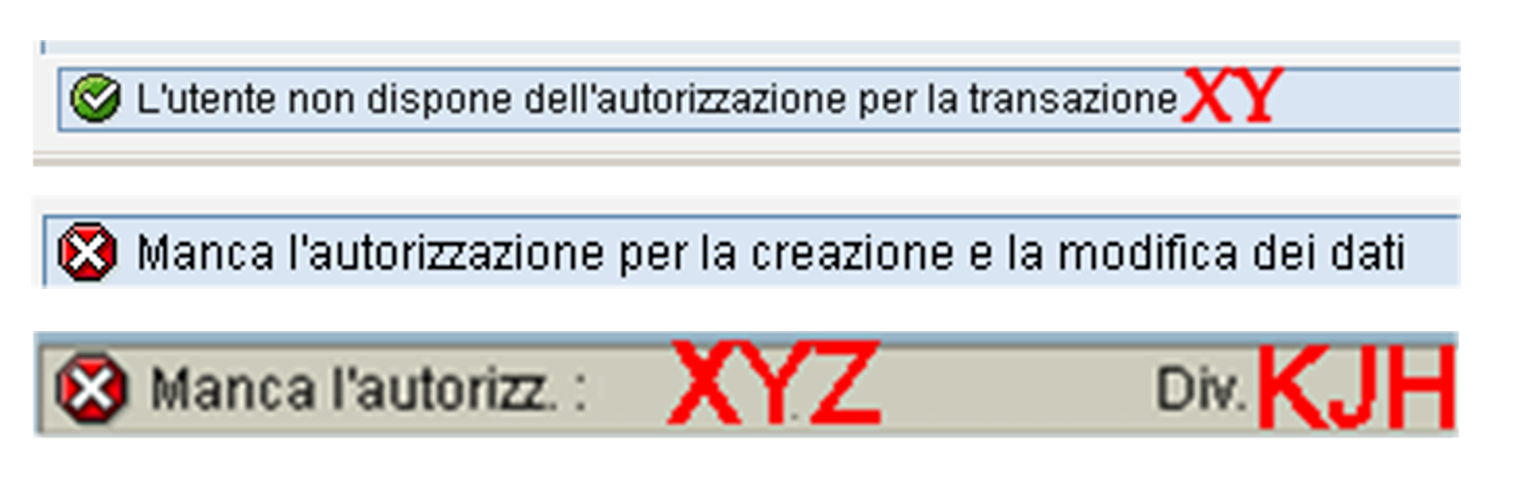
- Management of SAP security requests (User and Profile Management), preventive SOD analysis runs (in or
- der to limit the introduction of risks during the ordinary management of permissions). In SAP ECC or S/4HANA systems.
- Management of licensing of SAP systems
- Management of small evolutions and support for ongoing projects
- Support for the governance of SAP systems (i.e. periodic control activities of systems agreed with the customer)
- Maintenance of SAP GRC
What can be the metrics?
- Fixed monthly fee. A fixed fee per month, without limitation on the number of reports
- Type of ticket. A lump sum based on the type of ticket shared together with the customer's needs
- At consumption. That is, the sum of the time taken to resolve all managed reports
Why is it important to have a ticketing system?
There is now a ticketing system in all organizations. These systems are important for:
- classify the various cases of error
- correctly address the problem is notifications
- adopt service level agreements SLA service levels
- track the entire lifecycle of requests for audit purposes
Don't have an active ticketing system? You can use ours!
Why are the certifications of the company offering the service important?
Normally, support contracts are defined as access channels between vendor and customer. This involves contact with sensitive and/or sensitive information.
It is therefore essential that the chosen partner demonstrates that it has established a formal model of information control and security. The easiest way to check is to obtain supplier certifications. With particular regard to data security issues, e.g. ISO 27001.
The certifications of the resources that will put the systems in hand are also important.
How can Aglea help you?
We have created a business unit dedicated to the outsourcing support of SAP security. At the moment we follow more than thirty companies. From companies of a few dozen users to companies with several tens of thousands of users in the various sectors (e.g. Manufacturing, media, chemical, food and beverage, pharma)
We are certified:
- ISO 9001 (Design and provision of consulting services in the SAP security field. Provision of auditing, application management and technical support services in sap security (EA 33)
- ISO 27001 (Information Security Management in Consulting, Auditing, Application Management and Technical Support Services in SAP Security (EA 33)
- SAP Governance Risk and Compliance REX
Look at our certifications.
That's why the SAP SECURITY AMS service can be beneficial:
- The resources used in the support are highly specialized on the subject
- The specializations and experience of the security SAP group allow to anticipate any problems during the design of the activities
- The number of resources located territorially in different cities allows to have a continuity of service
- The number of resources allows to guarantee constant coverage during the year, even in periods of vacation / illness
- We have our own ticketing tool, if the customer does not own one, otherwise we work in the ticketing system made available to the customer
- The service allows you to segregate your business activities. The management of roles and utilities is segregated from other functions
- The ability to track and document all requests makes it easier in the event of an audit to produce the various evidence
- You can activate in the segregation of duties SOD preventive logic service and monitoring of the planned compensatory controls
- We manage SAP security from ECC systems to S/4HANA systems in addition to most SAP systems
Read our AMS security SAP case histories here.
Suggested Post from our SAP Security Blog
SAP AMS come prepararsi?
- Come ti puoi preparare per capire se ti conviene usufruire di un servizio AMS Security SAP?
- Leggi e scarica la checklist completa per valutare se il servizio fa per la tua azienda.