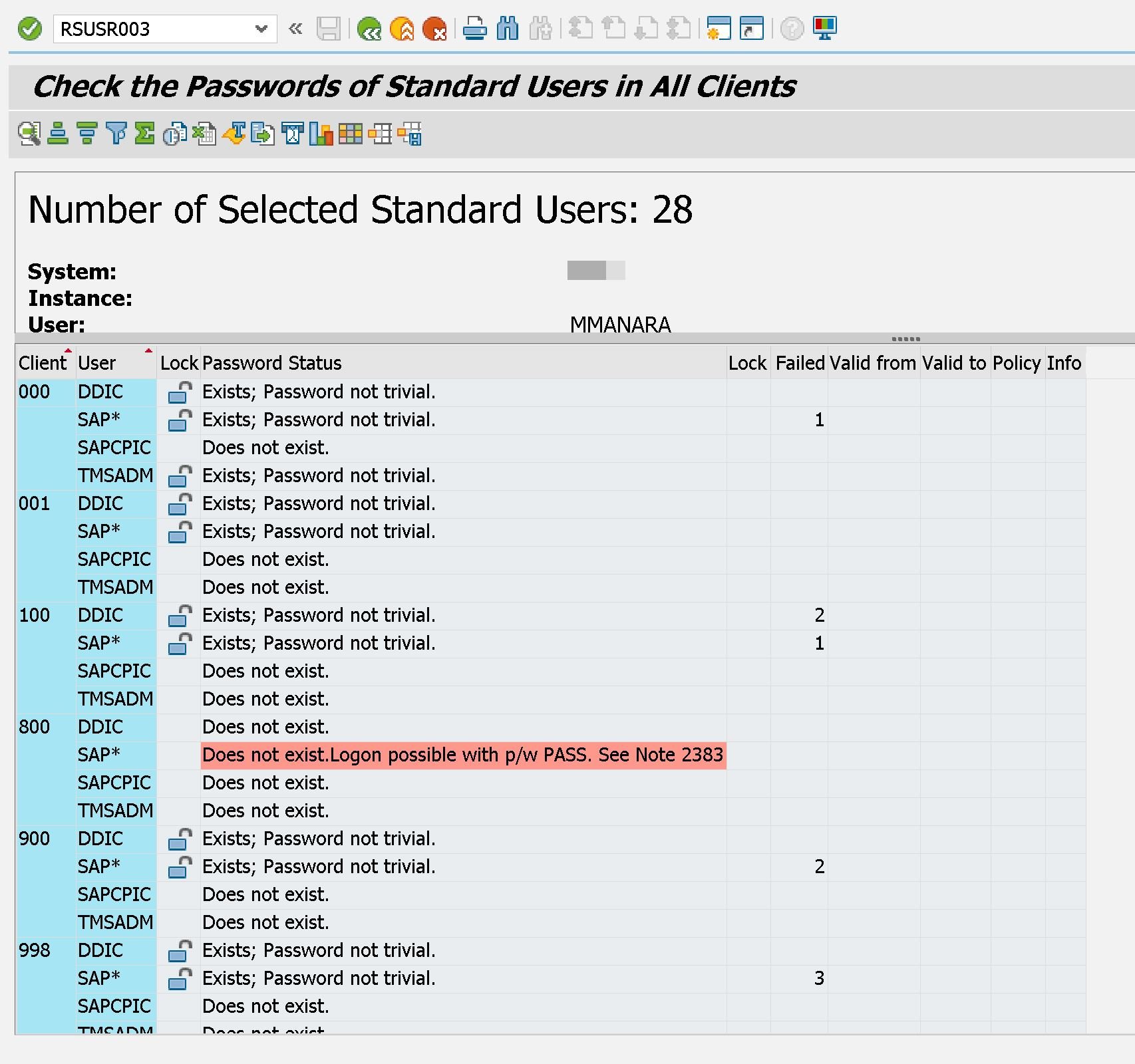
Did you know that there are "special" SAP users whose credentials are known, public?
This is not an SAP oversight; it is something known and familiar. Especially in the initial setup processes of the system, utilities are activated that should be secured immediately thereafter. But what are they and what should you do?