Are you oriented to buy SAP Governance Risk and Compliance Access Control? You could also interest to suggestions for the purchase, configuration and the management of this tool

1. 1. WHAT IS THE LICENSING?
First of all, it’s important to identify what we are talking about. SAP GRC it’s an acronym (Governance Risk and Compliance) that combines different SAP systems. There are several systems that are under this area. The main ones are the following (there are others):
- Access Control (AC)
- Process Control (PC)
- Risk Management (RM)
- Nota Fiscal Elettronica (NF-e)
- Global Trade Service (GTS)
- Health and Safety (EHS)
- …
The first three are certainly the best known once. Furthermore, despite being three distinct but strongly correlated systems, they are all installed together through a single installation package called the GRC foundation. The technical name is GRCFND.
As already said, in order to install these systems, usually in an ad hoc ABAP system, connected to the backend systems to analyze (such as DAP ERP, CRM, SRM or other legacy systems) you need to buy the license individually.
Here are the metrics for SAP licenses. Here are metrics for SAP GRC AC, PC e RM
2. WHICH MODULES SHOULD BE ACTIVATED FIRST?
SAP GRC Access Control is made of four main modules, hereafter the various names in the releases of SAP GRC Access Control.
.
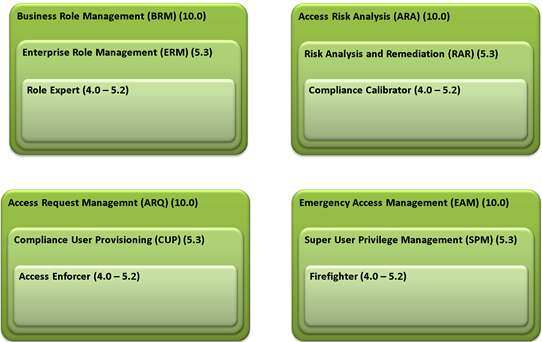
The last available release at the moment is the 12th ( SAP GRC 12) which maintain names of the 10.x.’s components.
- Access Risk Analysis (ARA) (10.0)
- Emergency Access Management (EAM) (10.0)
- Business Role Management (BRM) (10.0)
- Access Request Management (ARQ) (10.0)
In the previous releases the names have changed, probably for commercial reasons, while maintaining substantially the same functionality.
Usually, the GRC access control process of configuration follow these steps:
- Having define a SoD matrix (ruleset) the Access Risk Analysis is activated
- The component “Firefighter” Emergency Access Management (EAM) is activated below
Following this, in this case is a good idea to check the state of health of your authorization concept and active security procedure the remaining modules:
- Access Request Management (ARQ)
- Business Role Management (BRM)
All modules are connected to each other’s but there are not modules to be activated simultaneously.
We tell you about our experiences in the GRC area!
Contact us for a free advice!
3. If I don’t want to activate immediately the ARQ and BRM modules, what can I do?
SAP GRC uses a component called Risk Terminator in the implementation process.
This component, which resides in the ABAP part (in the backend) carries out a risk analysis on the roles assigned to the user and on the roles that are being built, in real time.
SAP suggests using this ARA sub-module only in the transition and completion phase of the ARQ and BRM modules.
4. Are there certifications for the system integrator?
If you want to use a system integrator there are two types of certifications, for SAP GRC Access Control consultants. The sequent:
And also, as a company in the SAP REX (SAP Recognized Expertise) Grc area program.
Ecco la pagina AGLEA per la certificazione REX di GRC.

Ecco la pagina AGLEA per la certificazione REX di GRC.
Always ask for references and be informed on which types of installations have been done and which SAP GRC modules have been realized. A configuration of the Access Risk Analysis (ARA) module can be quite different in terms of complexity from a configuration of the Access Request Management (ARQ) module.
GRC projects often require transversal skills, security, business, and even system skills.
Why should you ask to a supplier? The installation and the configuration of GRC it is not complicated in the majority of scenarios. By the way, it can happen that some choices taken without experiences could lead, in the long run, to a limit of the instrument. In almost all cases, these limits are due to lack of configuration or improper use of the functions provided by SAP.
5. Once GRC has been installed, how much does the management cost me?
SAP GRC must be a tool actually used in the company. This also involves an effort in terms of time and resources on the part of some company figures.
Which are the figures and the time required to devote to governance issues, in the context of SAP GRC Access Control, depends on the complexity and the modules implemented.
We can say that using only ARA and EAM modules, these figures are required:
- ARA
- Risk Owner (business involvement)
- Function owner (necessary in case of approval workflow)
- Reference ICT
- EAM
- Controller and Owner of super users (ICT or Business) must have a SAP, mostly the owner
- IT reference for the module
In the case of use ARQ and BRM modules, involvement can be much greater, however this depends on how the approval workflows are implemented.in general, SAP GRC Access Control installations do not require custom developments. This makes the tool very easy to manage, especially during upgrades or new customizations.
6. How can I prepare myself?
1) Identify the supplier to request support, see point 4
2) Define a SoD matrix, don’t forget about the custom ones.
3) Identify who the owners might be
4) Define SAP security processes on paper (simulate activating them, even without a role). Remember that the more complex they are, the harder they will be to manage and the longer lasting (before the various approvals).
5) Attend the GRC 300 course in SAP o learn more about the features of the SAP GRC Access Control
6) Perform an audit of your systems to see if they are already compatible with the logic proposed by SAP GRC.
Blog post originally translated from: https://www.aglea.com/blog/6-suggerimenti-prima-di-installare-sap-grc-access-control
