Those areas that are often poorly guarded, when you send emails, may contain sensitive or personal data in the body of the email or in the attachments.

In SAP there is a feature to see all outgoing mails from SAP, also in content terms. Let us see what it is and why it is often underestimated in terms of security.
How to send email from SAP?
There is a specific module that allows to send email in SAP, it's called SAP Office.
Through SBWP Transaction (SAP Business Workplace), see image above, which is often correctly inserted in the base role issued to all SAP users, it's possible to receive and/or send emails. There are different types:
- External Address
- SAP Logon Name
- FAX
- Business Partner
- etc..
The above, clearly represents the end-user mode.

However you can also use the mail management functionality through programs. For example, once completed an elaboration (maybe run in the background), send an email notification to who had requested that particular activity.
What are SAP transactions for managing emails?
There are several, the main are the following:
- SBWP - SAP Business Workplace
- SOST - SAPconnect Send Requests
- SOSG - Send Request Overview (Groups)
- SOSB - Send Request Overview (Users)
- SCOT - SAPconnect - Administration
- SO1* SO2* SO3* transactions for example:
- SO01 SAPoffice: Inbox
- SO04 SAPoffice: Shared Folders
- SO23 SAPoffice: Distribution Lists
From the top down, for end-user management purposes, it’s kind of Microsoft’s Outlook inside SAP.
Up to management by mail administrators, for example SCOT transaction.
Probably the most underrated is SOST. That is the possibility to see the outgoing mails from SAP, regardless of who sent them. In the Sender column you can see who sent the email.
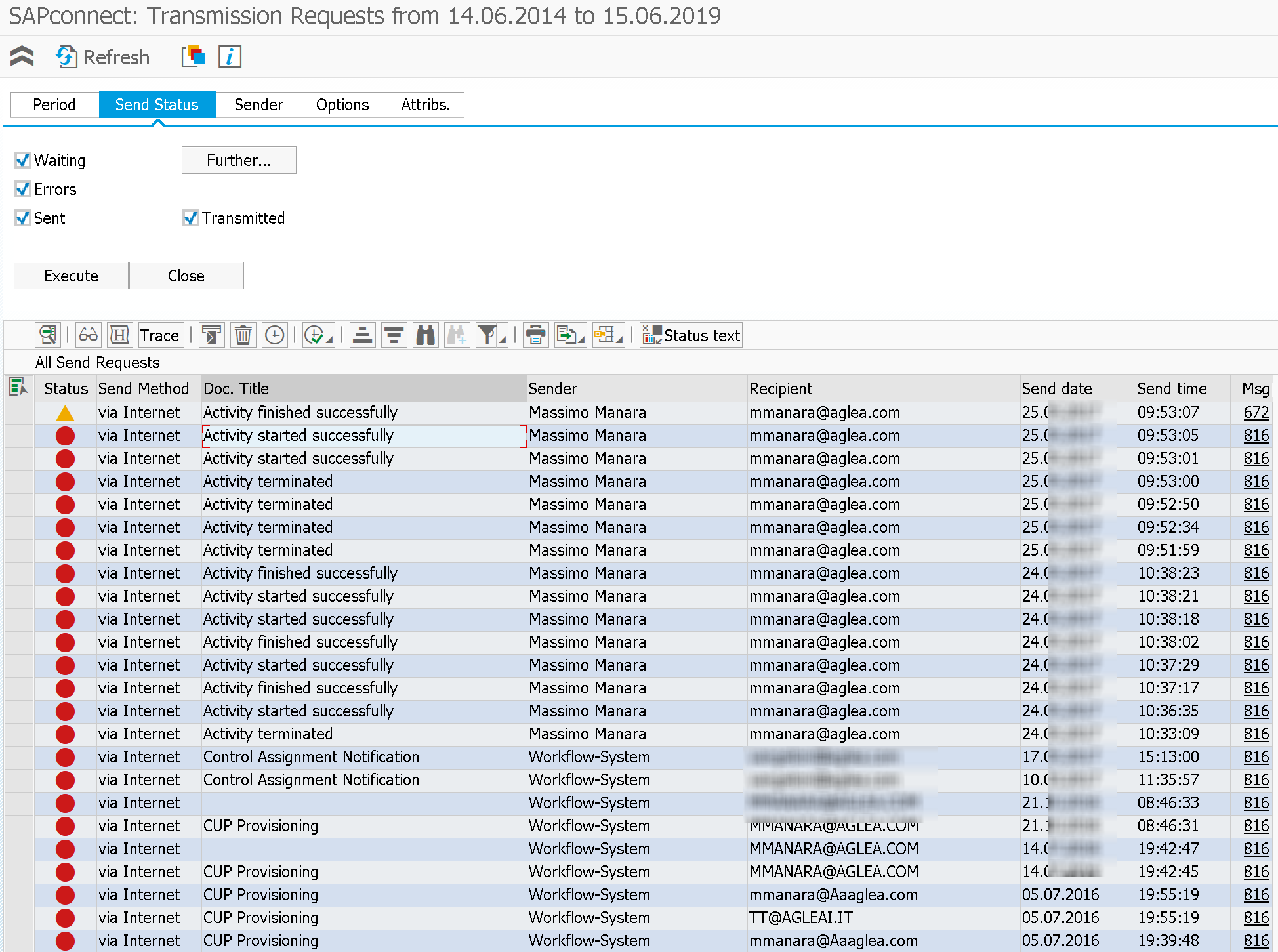
Through the selection of the email and the glasses button it's possible to visualize the contents.
What could be in the emails?
The emails' content can be the most disparate for example:
- Approval link, click on the link to access an approval portal. It depends if this portal carries out additional checks on the user who is approving
- In the body of the email. Obviously the actual content of the email may contain personal or sensitive information for the company that some people should not see
- In some contexts you can find solutions that send email containing password in clear. Also in this case the interception of these messages would involve the possession of credentials that could be misused.
- Attachments. Although the content of the email may be generic and harmless the attachment may not be so
Imagine finally the presence of a program for the discounts' calculation or the automatic sending of sensitive data to a limited number of persons.
The sender in this case could be a system user, but through SOST transaction it may be possible to see its contents.
How to check?
There may be different audits to be done:
- Verify that SOST transaction is not assigned to any end-user.
- Assess the segregation of those who have the possibility to send mail
- Analyze standard authorization objects to evaluate possible segregation, for example object S_OC_ROLE
- Avoid if possibile to classify the mail (sensitivity field) and pay attention in this case since the content is visible from administrator using tables or function module
About the second case above, imagine the following scenario:
An user, maybe form an external Company, who has a station without company mail but with access to SAP.
The latter could send emails using the SAP mail in absence of the corporate one.
Blog post originally translated from: https://www.aglea.com/blog/sap-mail-in-sap-tutti-leggono-le-mail-di-chiunque
